A cybersecurity agency says a preferred Android display recording app that racked up tens of hundreds of downloads on Google’s app retailer subsequently started spying on its customers, together with by stealing microphone recordings and different paperwork from the consumer’s telephone.
Analysis by ESET discovered that the Android app, “iRecorder — Display Recorder,” launched the malicious code as an app replace nearly a 12 months after it was first listed on Google Play. The code, in response to ESET, allowed the app to stealthily add a minute of ambient audio from the system’s microphone each quarter-hour, in addition to exfiltrate paperwork, internet pages and media recordsdata from the consumer’s telephone.
The app is not listed in Google Play. You probably have put in the app, it’s best to delete it out of your system. By the point the malicious app was pulled from the app retailer, it had racked up greater than 50,000 downloads.
ESET is looking the malicious code AhRat, a custom-made model of an open-source distant entry trojan known as AhMyth. Distant entry trojans (or RATs) benefit from broad entry to a sufferer’s system and might usually embody distant management, but in addition perform equally to spy ware and stalkerware.
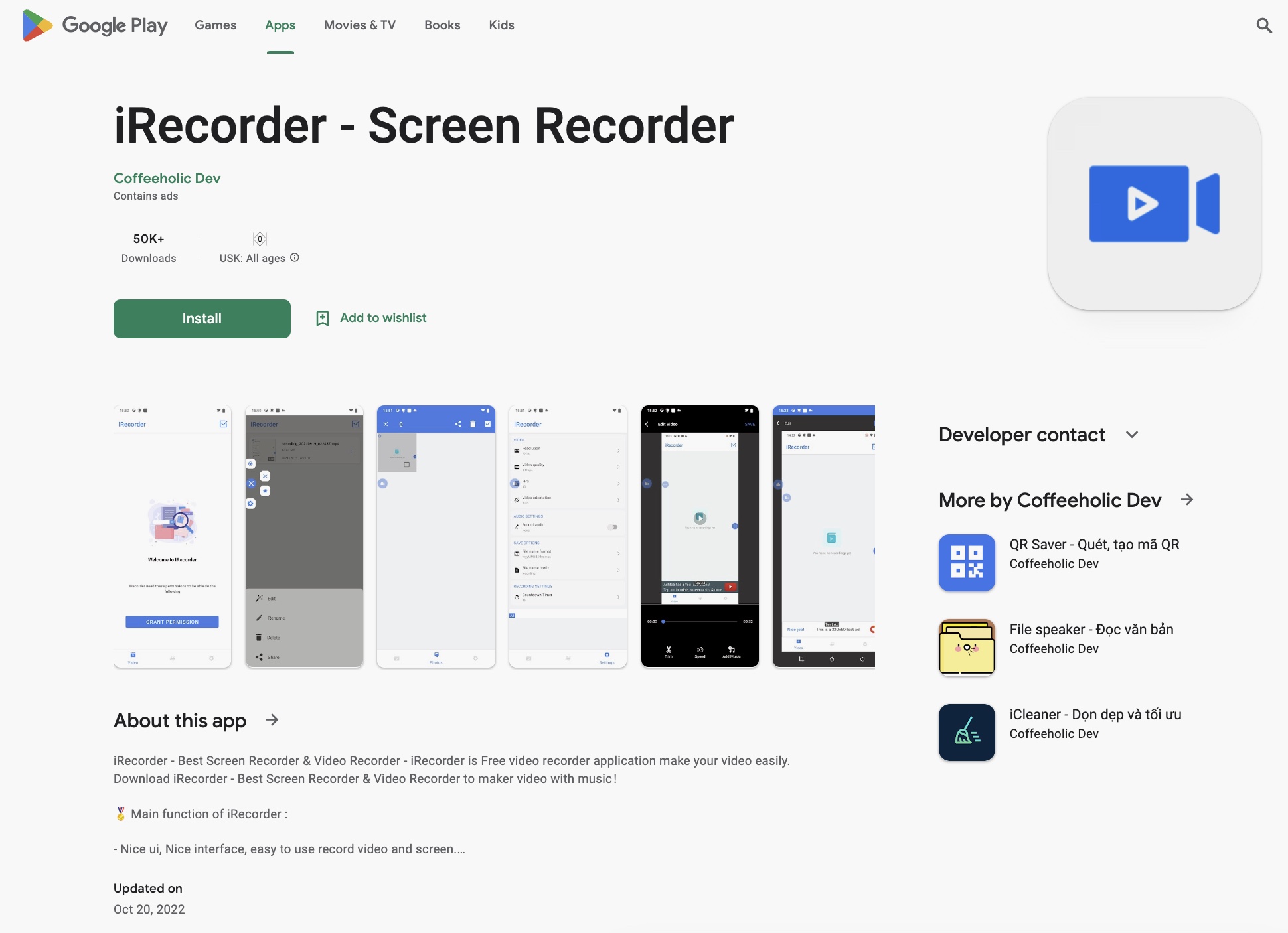
A screenshot of iRecorder listed in Google Play because it was cached within the Web Archive in 2022. Picture Credit: TechCrunch (screenshot)
Lukas Stefanko, a safety researcher at ESET who found the malware, mentioned in a weblog put up that the iRecorder app contained no malicious options when it first launched in September 2021.
As soon as the malicious AhRat code was pushed as an app replace to present customers (and new customers who would obtain the app straight from Google Play), the app started stealthily accessing the consumer’s microphone and importing the consumer’s telephone knowledge to a server managed by the malware’s operator. Stefanko mentioned that the audio recording “match inside the already outlined app permissions mannequin,” on condition that the app was by nature designed to seize the system’s display recordings and would ask to be granted entry to the system’s microphone.
It’s not clear who planted the malicious code — whether or not the developer or by another person — or for what motive. TechCrunch emailed the developer’s e mail tackle that was on the app’s itemizing earlier than it was pulled, however has not but heard again.
Stefanko mentioned the malicious code is probably going a part of a wider espionage marketing campaign — the place hackers work to gather info on targets of their selecting — generally on behalf of governments or for financially motivated causes. He mentioned it was “uncommon for a developer to add a legit app, wait nearly a 12 months, after which replace it with malicious code.”
It’s not unusual for unhealthy apps to slide into the app shops, neither is it the primary time AhMyth has crept its method into Google Play. Each Google and Apple display apps for malware earlier than itemizing them for obtain, and generally act proactively to pull apps once they may put customers in danger. Final 12 months, Google mentioned it prevented greater than 1.4 million privacy-violating apps from reaching Google Play.